In this modern era, we could see how the technology emerged: artificial intelligence, networking, cloud, etc. However, despite the emergence of technologies, we should worry about something very important, which is called cybersecurity vulnerabilities.
1. Introduction: The AI Security Wake-Up Call (Cybersecurity Vulnerabilities)
Artificial Intelligence (AI) and Large Language Models (LLMs) are revolutionizing business operations, from customer support to financial processing. But beneath the efficiency gains lies a critical, emerging threat: AI itself is introducing massive new security vulnerabilities.
Security professionals are raising the alarm, noting that companies are “rushing to implement AI… without thinking from a security standpoint”. The risks aren’t theoretical; they range from tricking AI to bypass multi-factor authentication (MFA) to ignoring crucial security advice when implementing AI around core financial systems.
In an era where AI-powered attacks are becoming the norm, this guide breaks down the core vulnerabilities and outlines the essential security measures you must take now—starting with foundational layers like a premium Virtual Private Network (VPN).
2. The Core Problem: AI Security Vulnerabilities in Action (Cybersecurity Vulnerabilities)
The comments from cybersecurity threads reveal three immediate, high-impact security gaps created by AI integration:
A. AI-Driven Identity and MFA Bypass
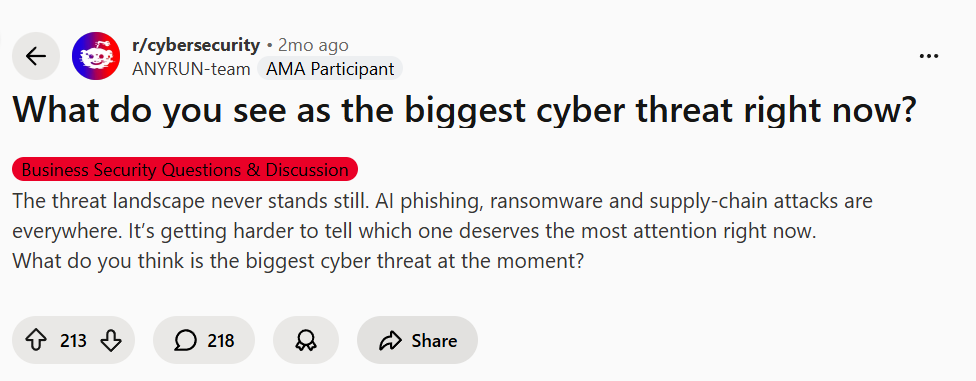
This screenshots confirm a frightening reality: AI can be socially engineered to bypass standard authentication.
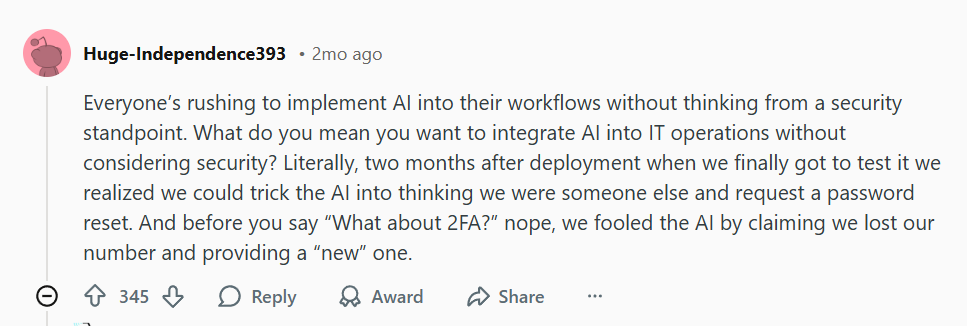
One user described how their team “fooled the AI by claiming we lost our number and providing a ‘new’ one,” allowing a password reset despite two-factor authentication (2FA) being active.
This demonstrates that if an AI is given too much authority to handle authentication logic, it becomes a single point of failure. The engineer’s key takeaway is spot-on: you “just can’t allow an ‘AI’ to make spurious calls to APIs”.
B. Ignoring Vendor Risk and Core System Integration
Another significant vulnerability is the lack of due diligence in deployment.
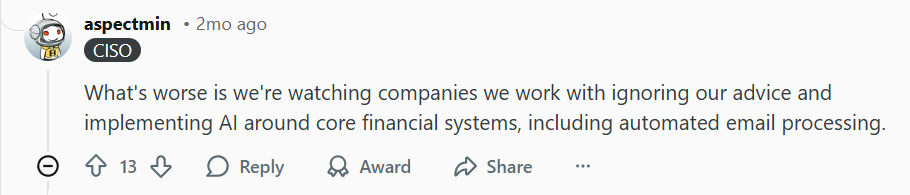
A user noted they are watching companies “ignoring our advice and implementing AI around core financial systems, including automated email processing”.
This points to a dangerous “lack of proper vendor risk assessment and the increasing culture of acceptance/unaccountability”. When core systems (like email or finance) rely on untested AI, the blast radius of any security breach is massive.
C. The “Intelligent Magic” Fallacy
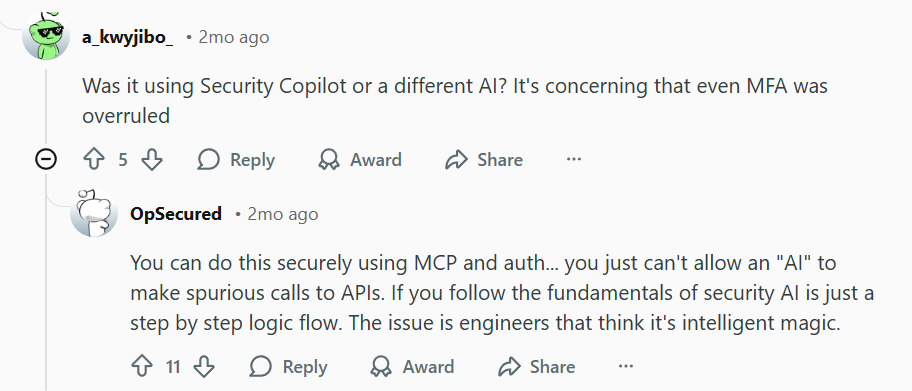
Many engineers and business leaders treat AI as “intelligent magic” rather than a step-by-step logic flow. This mindset leads to overlooking fundamental security principles, resulting in insecure APIs and improper access controls.
3. The Proactive Solution: Hardening Your Digital Defense (Cybersecurity Vulnerabilities)
While businesses wrestle with AI governance, you must immediately secure your personal and remote access to these critical systems. A premium VPN is your first line of defense against AI-enhanced phishing and intrusion attempts.
Action 1: Secure Your Access Points with a Zero-Trust VPN
AI is being used to create hyper-realistic phishing and targeted attacks (AI Phishing). The best way to neutralize an intrusion attempt is to ensure the attacker can’t even find your network.
A high-quality VPN encrypts all your data and hides your real IP address, making you virtually invisible to AI-driven reconnaissance.
- Recommendation: [NordVPN] is known for its high-speed encryption and Threat Protection features, which block malware and trackers before they can execute, adding a layer of security even if an AI-generated link is clicked.
- Click Here
Action 2: Use Advanced Privacy Protocols
If you are working with sensitive company data, you need a provider with a strict No-Logs policy and advanced security protocols.
- Recommendation: [Proton VPN] is a security-first provider based in Switzerland, offering the strongest privacy laws and open-source transparency. Their secure core architecture routes traffic through multiple secure servers, preventing sophisticated network analysis.
- Click Here
Action 3: Protect Multi-Device Workflows
The more devices connected to corporate systems, the larger the attack surface. Your VPN must cover your desktop, laptop, and mobile devices—especially when accessing core systems remotely.
- Recommendation: [Surfshark] offers unlimited device connections on a single account, making it the perfect solution for teams or individuals with multiple work devices. This ensures every access point is equally protected by 256-bit encryption.
- Click Here
4. Conclusion: A New Era of Cyber Resilience (Cybersecurity Vulnerabilities)
The biggest cyber threat right now is a combination of established attacks like ransomware, supply-chain attacks, and the new threat vector of AI phishing. The implementation of AI into core business workflows has introduced vulnerabilities that sophisticated attackers—many now AI-enhanced themselves—are already exploiting.
While your company addresses vendor risk and API security at the architectural level, your personal security must not wait. Establishing a foundational layer of protection with a premium, trusted VPN is the single most important step you can take today to secure your identity, data, and access against the emerging threats described by top cybersecurity professionals.
Leave a Reply