We often imagine hackers as shadowy figures typing complex code in dark rooms, exploiting intricate software vulnerabilities. While that happens, the reality of modern cyber threats is far more insidious and personal. As one security specialist noted when trying to understand hackers, the question arose: “How much social engineering is really needed?”
The answer from the security community is stark. This shift changes everything. It means that even if your software is perfectly patched, a single moment of human error—a clicked link, a convincing fake login page—can bypass millions of dollars in technical security.
One experienced user emphasized the scale of this threat:
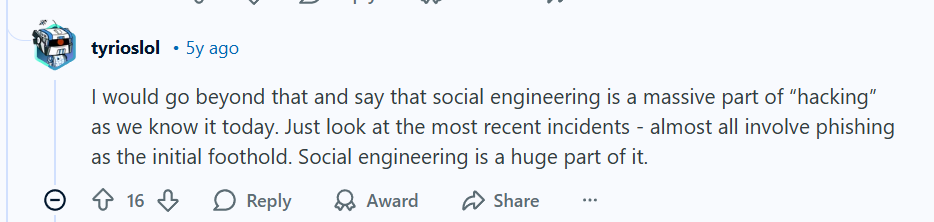
Another commenter highlighted how effective this approach can be, even with minimal technical expertise:
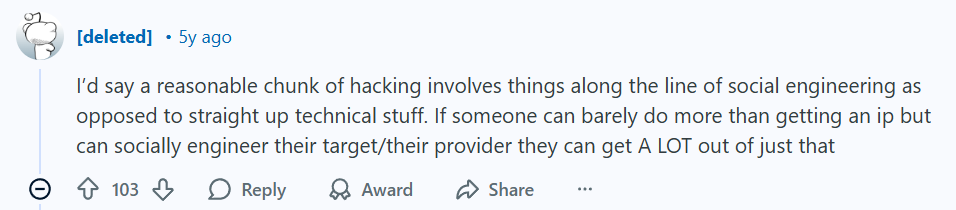
So, if the threat landscape now targets the human as the weakest link, how do we build a personal defense that is always on, always vigilant, and operates beyond just awareness? The answer lies in a fundamental tool: a robust Virtual Private Network (VPN).
The Human Firewall Needs a Technical Shield
You are the first and last line of defense. “Don’t click suspicious links” is crucial advice, but modern phishing attacks are sophisticated. They mimic your bank, your cloud provider, or even internal company communications perfectly.
This is where a VPN provides its first, often overlooked, layer of value: protection on untrusted networks. Imagine you’re at a coffee shop and connect to “Free Cafe WiFi.” A hacker on that same network can easily set up a fake hotspot or intercept unencrypted data—a classic “social engineering” trick for your device. A VPN like NordVPN, Surfshark, or ProtonVPN creates an encrypted tunnel for all your data, making it unreadable to any eavesdropper on that network. It neutralizes this common physical social engineering trap.
Masking Your Digital Footprint: Making You a Harder Target
Social engineering often starts with reconnaissance. An attacker might gather information about you—your IP address, rough location, internet service provider—to make a phishing email more convincing (e.g., “We noticed suspicious activity from your IP in [Your City]…”).
A premium VPN directly counters this. By masking your real IP address and replacing it with one from its server network, services like NordVPN, Surfshark, and ProtonVPN significantly reduce the data points available for these personalized attacks. You become a harder, less visible target. As the forum insights suggested, stopping an attacker at the “getting an IP” stage is a significant win.
Proactive Privacy as a Core Principle
Choosing a VPN is about adopting a philosophy of proactive privacy, not just reactive security. It’s the digital equivalent of locking your door every time you leave, not just when you think the neighborhood is dangerous.
- NordVPN offers a suite of threat protection features that block malicious websites and trackers before they even reach your browser, adding a pre-emptive filter against phishing links.
- Surfshark provides unlimited simultaneous connections, allowing you to protect every device in your household—because a hacker might target the least tech-savvy person in your home as the easiest entry point.
- ProtonVPN, built by the team behind Proton Mail, is founded on a strong ethos of privacy and transparency, operating under Swiss privacy laws. It’s an excellent choice for those who prioritize principle-driven security.
The Essential Layer in a Multi-Layered Defense
No single tool makes you invincible. Security requires layers: strong, unique passwords (use a password manager!), two-factor authentication, updated software, and critical thinking to spot social engineering.
A VPN is the indispensable layer that secures your connection, hides your traffic, and protects you on any network. It works silently in the background, providing a technical countermeasure to attacks that exploit human psychology and insecure infrastructure.
Conclusion: Don’t Wait for the Phish to Bite
The consensus from security discussions is clear: social engineering is not a minor trick; it’s the primary weapon in the modern hacker’s arsenal. Defending against it requires more than just caution; it requires smart, automated tools that extend your capabilities.
Investing in a reliable VPN service—whether you choose the feature-rich NordVPN, the value-packed Surfshark, or the privacy-centric ProtonVPN—is no longer an option for just the tech-savvy. It is an essential step for anyone who values their security and privacy in an online world where the greatest vulnerability sits between the chair and the keyboard.
Ready to build your essential layer of defense? Explore NordVPN for advanced threat protection, check out Surfshark for unlimited device coverage, or consider ProtonVPN for its strong privacy principles. Take control of your online security today.
Leave a Reply