The digital landscape is evolving at a staggering pace, and with it, the nature of online threats is transforming. In cybersecurity discussions, experts are already looking ahead, warning that the coming years won’t just be about more sophisticated malware—they’ll be about more attack surfaces, more automation, and more human vulnerability. As one analyst put it:
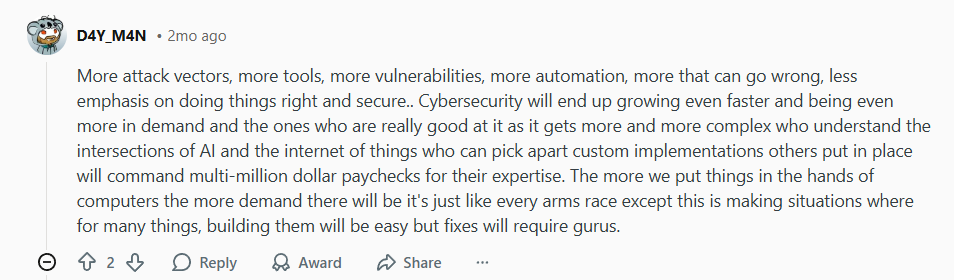
This paints a clear picture in cybersecurity: as technology grows more complex, so do the risks. But what does that mean for everyday users? And in a world where AI and automation dominate the conversation, where does human responsibility fit in?
The Double-Edged Sword of Automation in Cybersecurity
There’s a growing reliance on AI-driven security tools, but experienced professionals caution against over-automation. One deleted but insightful comment highlighted a critical truth:
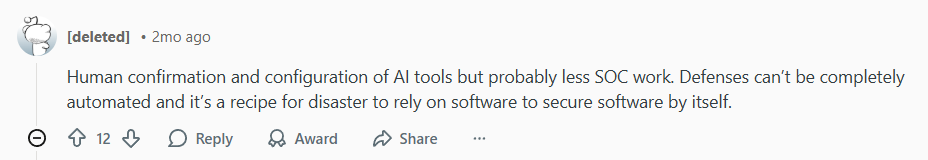
This is a crucial reminder: software alone cannot fully secure software. AI can detect patterns, filter threats, and respond at machine speed, but human oversight—confirmation, configuration, and critical thinking—remains irreplaceable. This is especially true as attacks become more personalized and socially engineered.
The Unchanging Weakest Link: You
Despite advances in AI and defensive tech, one harsh reality remains unchanged: the majority of successful breaches don’t start with a complex zero-day exploit. They start with a simple human mistake. As another user bluntly stated:
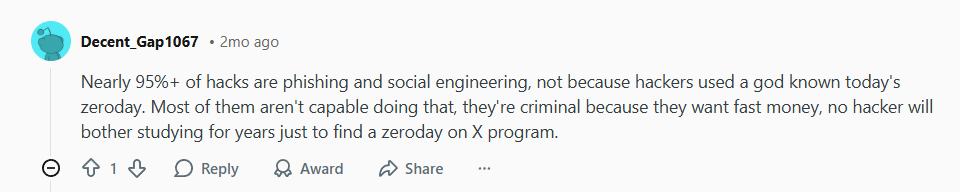
Phishing, pretexting, and social engineering account for the overwhelming majority of breaches. Criminals aren’t always master coders—they’re opportunists looking for the fastest path to money or data. And that path often runs straight through an inbox, a direct message, or a cleverly spoofed login page.
What This Means for Personal and Business Cybersecurity
The intersection of these trends tells us two things:
- Defense must be layered and intelligent—combining AI tools with human vigilance.
- Protection must start long before a phishing link is clicked—at the network and connection level.
This is where tools like VPNs stop being “nice-to-haves” and start becoming foundational components of modern digital hygiene.
How a VPN Fits into the Future Cybersecurity Stack
1. It Secures the Connection, Not Just the Endpoint
While endpoint security (antivirus, firewalls) is vital, a VPN protects your data in transit—especially on unsecured or public networks where man-in-the-middle attacks and session hijacking are common.
2. It Reduces Attack Surface
By masking your real IP address, a VPN makes it harder for attackers to target you specifically based on location or ISP data—information often used to personalize phishing attacks.
3. It Complicates Tracking and Profiling
With widespread data collection fueling both ads and targeted attacks, a VPN helps obscure your digital footprint, making you a less visible and less attractive target.
4. It’s an Automated Layer That Works 24/7
Unlike manual security steps, a reliable VPN operates continuously in the background, encrypting traffic without requiring user intervention—a set-and-forget layer of always-on security.
Building Your Personal Cybersecurity Posture for 2025 and Beyond
In a world where both attacks and defenses are growing more automated, your strategy should be balanced:
- Use AI-enhanced tools for detection and filtering.
- Keep human awareness sharp—question unexpected messages, verify requests, and stay educated on common scams.
- Implement foundational privacy tech like VPNs to secure your connection by default.
- Encrypt, back up, and authenticate—make multi-factor authentication (MFA) mandatory wherever possible.
Choosing a VPN for Future-Ready Cybersecurity
Not all VPNs are built for the evolving threat landscape. Look for providers that offer:
- Strong encryption standards (WireGuard, OpenVPN)
- Integrated threat protection (malware and phishing site blocking)
- A strict no-logs policy
- Reliable speeds and stable connections
- Transparency and a proven track record in privacy
Recommended VPNs for robust, forward-looking protection:
- NordVPN—With Threat Protection and Meshnet features, it’s built for modern threats.
- Surfshark—Offers antivirus integration and alert systems for comprehensive security.
- ProtonVPN – Emphasis on privacy, transparency, and advanced VPN technologies.
Final Thought: Cybersecurity Is a Mindset, Not Just Software
As we move into an era of AI-driven attacks and automated defenses, one principle remains timeless: security is a shared responsibility between technology and people. Tools like VPNs provide essential protection at the network level, but they work best when combined with informed, cautious online behavior.
Don’t wait for the next wave of attacks to upgrade your defenses. Start with a secure foundation today.
Ready to future-proof your online presence? Explore how NordVPN can serve as your always-on first layer of defense, or check out Surfshark for all-in-one security. For those prioritizing privacy above all, ProtonVPN offers a transparent, principle-driven alternative.
Leave a Reply